Introduction
The stable and reliable card internal operating system is the basis for the normal operation of the smart card. The smart card operating system controls the communication between the outside world and the smart card, manages the storage space of the card, and processes various commands in the card, so the COS development process It is necessary to conduct a full and comprehensive test of COS. The main features of COS: It is a dedicated system; COS is generally designed and developed according to the characteristics and application scope of a certain card, with high reliability; the functions to be completed by COS are subject to relevant international norms and industry specifications; Application-type COSs often follow the same specifications, which makes COS testing somewhat reusable.
The above characteristics determine that conventional software testing methods cannot be directly used for COS testing.
1 smart card operating system
1. 1 COS structure
The main functions of COS are to pass and pass data from smart cards, control execution of related commands, manage and maintain file systems, and manage and execute encryption algorithms. Its structure can be divided into two levels: the functional layer and the microkernel layer.
The functional layer mainly implements the business logic of COS, and includes four modules: communication management, security management, command interpretation, and file management.
1) Communication management module: Perform parity check on the data received in the input buffer, and judge the correctness of the packet length, etc., but do not judge the content of the information. The command structure in ISO/IEC 7816-4 is used. The standard of judgment; receives the data after command processing, file management processing, and security authentication, and packages it into a complete result message according to the command structure requirements in ISO/IEC 7816-4, puts it into the output buffer, and sends it Result message.
2) Security management module: Accept the scheduling of the communication management module, and return the processed information to the communication management module; perform security verification on the data received by the communication management module, but do not verify the data content, if the security verification fails, directly Return verification failed.
3) Command interpretation module: Accept the scheduling of the security management module, and return the processed data information (response code corresponding to the command) to the security management module; need to authenticate on the data content (check whether the parameters of the command are Correct), and then perform the corresponding operation to complete the operation of the data in the card. If the data content authentication fails, the error code is directly returned to the communication management module.
4) File management module: Accept the scheduling of the command management module; The data exists in the form of files in the card. The file management module must provide basic operations such as file creation, modification, and deletion, and security control of file access.
The main function of the microkernel: Provide hardware support for the upper layer of the functional layer to realize communication between the terminal and the hardware inside the card. The microkernel is divided into an interface layer and a driver layer. The interface layer provides services for the function layer, and translates the service request of the function layer into a call to the driver layer to provide a unified interface for the function layer. The driver layer mainly implements various driving operations on the underlying hardware.
1. 2 COS state transition process
Each functional module may also need to make requests to other functional modules during the completion of a specific request. Between each module is the relationship between scheduling request and data response. In a pair of relationships, the scheduling request is expressed as the output of the module, the data response is represented by the input of the module, the scheduling and response are represented by transactions, and the transaction represents a set of data. And the manipulation of the data.
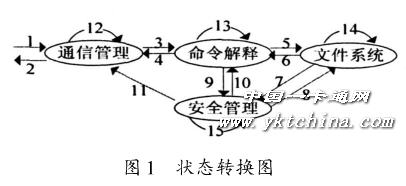
The state transition diagram during the system request/response process, as shown in Figure 1.
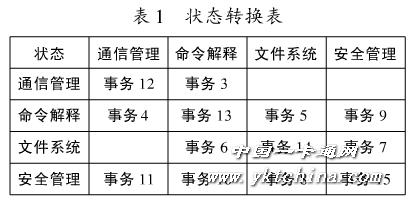
The corresponding status table is shown in Table 1.
Transaction 1: The smart card receives the APDU request from the terminal;
Transaction 2: APDU response sent by the smart card to the terminal;
Transaction 3: After receiving the APDU command, the communication management module calls the command interpretation module to process the APDU command.
Transaction 4: The command interpretation module returns the processed data or abnormal event to the communication management module;
Transaction 5: The command interpretation module needs to access the file and call the file system module during the processing of the APDU command;
Transaction 6: The file system module returns the processed information to the command interpretation module;
Transaction 7: The file system module invokes the security module when it needs to perform security control on the file operation;
Transaction 8: The security management module invokes the file system module when it relates to security-related files;
Transaction 9: The command interprets the response event sent by the module to the security management module;
Transaction 10: The processing data request sent by the security management module to the command interpretation module;
Transaction 11: A response event or exception event sent by the security management module to the communication management module;
Transaction 12: The communication management module calls the COS microkernel to call the underlying hardware interface request to complete the APDU request sent by the terminal;
Transaction 13: The command interpretation module calls the COS microkernel to invoke the underlying hardware interface request to complete the security management module request;
Transaction 14: The file system module requests the underlying hardware interface to be issued to the COS microkernel to complete the security management module request;
Transaction 15: The security management module invokes the underlying hardware interface request to the COS microkernel to complete the security management module request.
1. 3 smart card communication process
The communication between the smart card and the terminal is achieved through a command-response pair. The terminal sends a command to the card (in the form of C-APDU). After the card receives the command, the COS processes the received command message, and then packages the processing result into a response message (in the form of R-APDU) and returns it to the terminal.
The C-APDU consists of two parts: a mandatory four-byte command header, represented by CLA, I NS, P1, and P2, and an optional variable-length conditional body. The number of bytes of data sent in the C-APDU is defined by 1 byte of L c , and the maximum number of bytes of the R-AP
Teaware is a broad international spectrum of equipment used in the brewing and consumption of tea. Many components make up that spectrum, and vary greatly based upon the type of tea being prepared, and the cultural setting in which it is being prepared. This is often referred to as the tea ceremony, and holds much significance in many cultures, particularly in northwestern Europe and in eastern Asia.
Description:
Usage: Liquor/Wine/Beverage
Material: Extra-flint, high-flint and flint glass
Technology: Machine made
Volume: 50 to 3000ml or as your requirements
Weight: 150 to 2000g and so on
Sealing type: Screw cap or cork
Painting: Any color as you requirement
Quality control: SGS, FDA, ISO9001, ISO14001
Deep processing: Silk screen, decal, spray painting, electroplating, frosting, sand blasting.
Delivery term: EXW, FOB, CIF
Payment terms: T/T
Lead time: New design drawing confirm within 3days, Sample mold within 20 days, bulk molds within 30 days, produce in bulk within 30 days
FAQ:
Q: Are you a manufacture or a trading company?
A: We are a manufacture which located in Chengdu city and Yibin city, Sichuan, China.
Q: Can you customize the products?
A: Yes, we are professional to customize glass bottle, we can design the new drawings and open the new molds according to your requirement.
Q: Do you provide free sample?
A: Yes, for cooperation sincerity, we are glad to provide you samples for free, but for new customer, the express cost need to be paid.
Q: What is your MOQ?
A: Our only standard for MOQ is a 40 feet container.
Q: How long is your sample lead time, mold need time and production lead time?
A: New design drawing confirm within 3 days, sample mold within 20 days, bulk molds within 30 days, produce in bulk within 30 days

Teaware
Opal Glass Teaware,Hot-baking Label Teaware,Glass Teapot Product,Glass Material Teaware Mug
SICHUAN YIBIN GLOBAL GROUP CO.,LTD. , https://www.globalglassbottle.com